RADIUS (Remote Authentication Dial-In User Service) integration allows organizations to authenticate users against an existing RADIUS-compatible system, such as a VPN gateway, firewall, or legacy authentication service. This is a powerful feature for enterprises that require secure, centralized user verification through a trusted protocol.
Overview
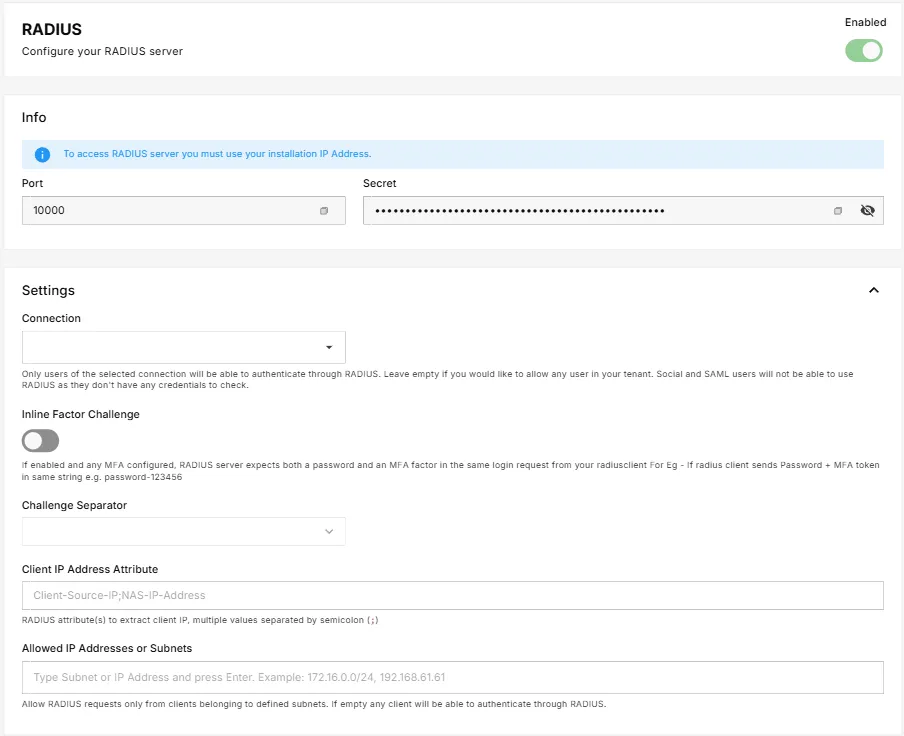
Once enabled, your tenant's RADIUS server will listen for authentication requests over a predefined network port and authenticate using a shared secret generated by the platform. These values are set by the IAM service and are not modifiable by the tenant.
To ensure security and seamless operation, the RADIUS server only accepts requests from IP addresses or networks explicitly authorized by you.
Enabling RADIUS Authentication
To activate RADIUS support for your tenant, simply toggle the RADIUS feature to Enabled in the integration settings and save. Once active, your tenant will accept RADIUS packets.
PlusAuth assigns a unique port and a secret to your tenant. These values are automatically provisioned and securely stored when you enable RADIUS. You can retrieve them from the RADIUS configuration screen, but you cannot modify them.
- IP Address: You must use PlusAuth installation's internal IP address to access the RADIUS server.
- Port: Used by RADIUS clients to send authentication requests.
- Secret: A secure shared key that must be configured in all RADIUS clients
Always ensure that RADIUS clients are configured to use the exact port and secret as provided.
Configuring RADIUS Server Behavior
Defining Specific Connection
You can scope RADIUS authentication to a specific connection within your tenant. If a connection is selected, only users within that connection will be eligible to authenticate through RADIUS. For example, you can select your AD//LDAP connection to only those users in your AD/LDAP with RADIUS.
Leaving this field blank allows any user with credentials in the tenant to authenticate. However, external users, such as social and SAML-based, are excluded, as these identities do not include native credentials that can be verified within PlusAuth.
Inline MFA Factor Support
For tenants with multifactor authentication (MFA) enabled, PlusAuth supports inline MFA challenges. When this option is enabled, users must supply both their password and MFA token in a single input string. This is particularly useful when the RADIUS client does not support Access-Challenge packets, which are used to facilitate multistep authentication flows.
For example, a user might enter:
myPassword-654321In this case, the platform expects the credentials to be separated by a specific character. You can configure this with Challenge Separator setting (e.g., a hyphen, colon, or space) to match your RADIUS client's formatting.
Client IP Resolution
In RADIUS packets, the client's actual IP address may not always be found in a single standard attribute, since different devices or network setups can send this information in different fields. To handle this variation, PlusAuth allows you to define which RADIUS attributes should be checked to determine the client's IP with Client IP Address Attribute setting.
One or more attribute names can be specified, separated by semicolons (;). They are evaluated in order, and the first attribute that contains a value will be used.
Example:
Calling-Station-Id;Framed-IP-Address;Client-Source-IPIn this example, the system first checks Calling-Station-Id. If unavailable, it continues with Framed-IP-Address, then Client-Source-IP, until a value is found.
IP Address Restrictions
To secure your tenant's RADIUS endpoint, you must specify which client IP addresses or network ranges are allowed to connect. This limits access to trusted RADIUS clients only.
You can enter individual IP addresses or CIDR ranges, such as:
192.168.1.10010.0.0.0/24If no IPs are defined, the platform will accept requests from all sources by default, leaving the RADIUS endpoint open to any client.
For better security, it is highly recommended to define specific IPs or CIDR ranges to restrict access to trusted sources.
Security Recommendations
For optimal security, it is important to follow several key practices.
First, NEVER share your RADIUS secret externally, as this could expose your system to unauthorized access.
Additionally, you should only allow connections from known client IP addresses or specific network ranges to minimize the risk of unauthorized clients gaining access.
Whenever possible, use Multi-Factor Authentication (MFA) to add extra layers of protection during authentication. Thanks to PlusAuth, even your clients does not support RADIUS Access-Challenge packets, you can still accept MFA challenges with Inline Factor Challenge feature.
Lastly, it's essential to periodically review the connection scope and IP restrictions to ensure that only trusted clients can connect and that your security settings remain up to date.